Combating the cyber heists that are costing the global economy
Posted By Shivangi Seth and Gatra Priyandita on June 8, 2023 @ 14:30

Across the world, governments and businesses depend on the transformative powers of digital technology to drive economic growth. Naturally, digitalisation leaves organisations, government agencies and consumers more vulnerable to cyber threats, including from states using digital technology to steal intellectual property for commercial gain—a practice known as economic cyber espionage.
But is there much that anyone can do about it?
Before we answer this question, it’s useful to consider how this threat is viewed in the international community. In November 2015, leaders of the G20 agreed [1] that states should refrain from economic cyber espionage. The agreement came in the midst of looming threats to the prosperity of nations—hackers, in many cases affiliated with states, were stealing billions of dollars’ worth of IP from universities and companies around the world. In the US alone, the annual cost of IP theft has been estimated at up to $600 billion [2].
But eight years on, the G20 agreement has had mixed results. Some countries are taking the issue seriously and have moved to attribute cases when states steal IP. For example, in 2018, the UK government held [3] China’s Ministry of State Security responsible for unleashing a ‘malicious cyber campaign’ that had been stealing IP in Europe, Asia and the US.
At the same time, cases have increased markedly in number, severity and scale (see Figure 1). Governments are uncovering more cases of cyber espionage, operations are harvesting greater amounts of IP and more firms in more countries across the world—including increasingly in emerging economies—are falling victim.
Figure 1: Number of reported incidents of state-sponsored cyber operations, 2009 to 2022
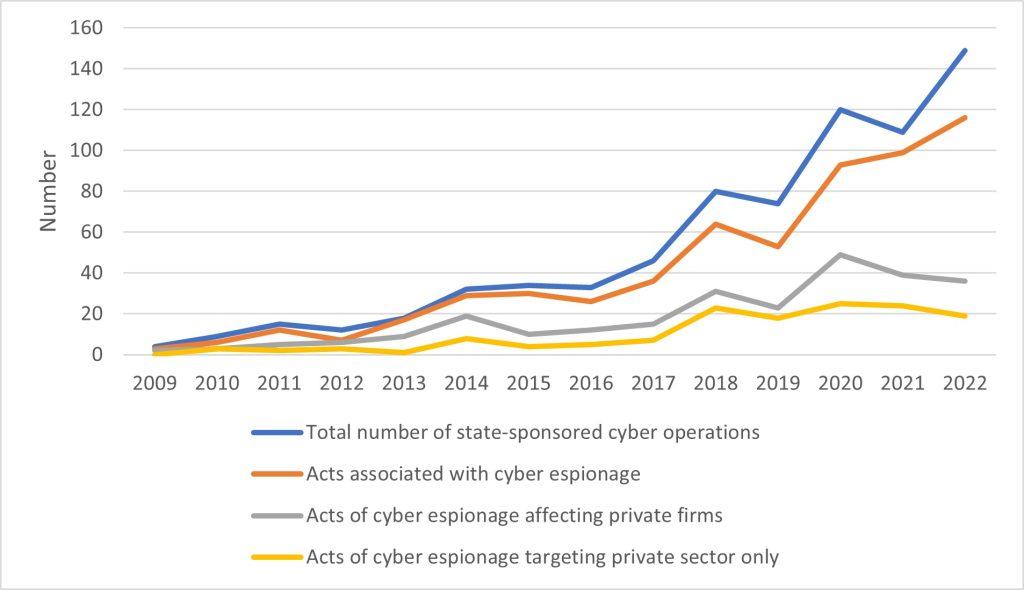
Source: Based on the Council on Foreign Relations’ Cyber Operations Tracker [4].
Given the worsening situation, it may be surprising that the issue hasn’t been given as much attention as other cyber-enabled threats like ransomware, cyberattacks on critical infrastructure, and denial-of-service attacks (a problem the G20 hasn’t discussed since the 2015 summit).
To a large extent, difficulties in addressing the threat of economic cyber espionage lie in attributing the attacks to a specific actor. The covert nature of these operations makes it hard to identify culprits with high enough confidence. Naturally, officials and investigators are faced with a long list of questions, like: how can we be certain that these hackers work for a state, or that they’re part of an organisation with strong connections to a state’s intelligence community? Even more difficult is identifying a hacker’s motivation; hackers—including those sponsored by states—hack for different reasons in different cases. And even if experts are certain that data was stolen, can they really be certain that it was given away to competing commercial firms?
Traditionally, experts look to hacking operations perpetrated by what’s known as ‘advanced persistent threats’, or APTs. In the hacking community, an APT is distinct because it requires considerable resources and is thus likely backed—or at minimum condoned—by a state actor.
But even if cybersecurity experts are certain about an APT’s hacking tactics, they may disagree over how closely affiliated the hacking group is with a particular state, or about its motivations. This is further complicated by the increasingly blurred boundaries between states and criminal gangs. APT 41 [5], for instance, is a hacker group that the US has identified as simultaneously conducting its own non-state-sponsored targeting of the video games industry alongside state-sponsored attacks that align with China’s industrial plans. Given the methodological challenges in calculating the costs of even physical forms of IP theft, there are added complexities in calculating the true costs of IP theft.
These challenges are further compounded by reluctance to examine the detection of cyber espionage campaigns for fear that publicity could harm the economy or create collective responsibility that companies are unwilling to commit to. Because attribution and cost-calculations in cases of IP theft are time-consuming and complex, governments can never be perfectly aware of just how urgently they need to combat it—especially given that many emerging economies invest heavily in the research and development of critical technologies [6], including biofuels and 5G networks.
The detrimental effects on innovation, job stability, national security and global competitiveness demand a concerted effort to address economic cyber espionage. APTs are increasingly aiming to disrupt global supply chains, and developing economies in the global south are likely to become the prime targets of IP theft in the coming years, given rapid economic growth. Based on our own assessments, while private enterprises in advanced economies still constitute the largest targets of cyber operations by states, there are increasing numbers of cases in developing economies (see Figure 2).
Figure 2: Geographic spread of state-sponsored cyber operations affecting private entities, 2014 and 2020
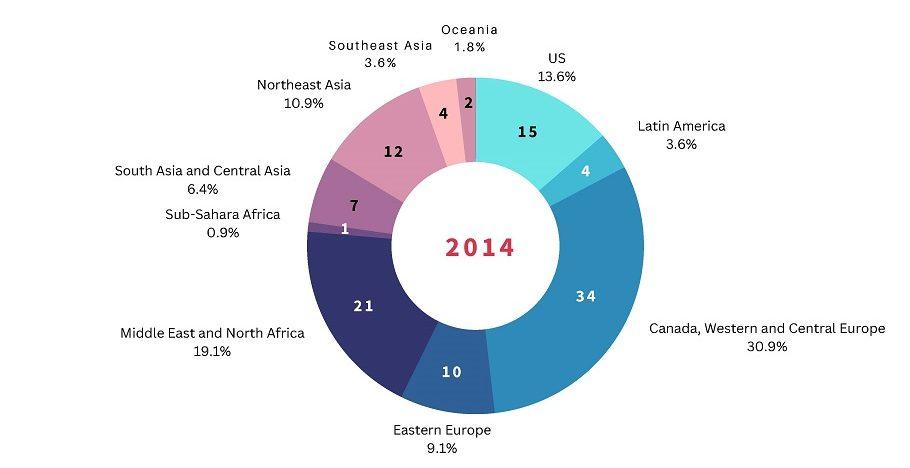
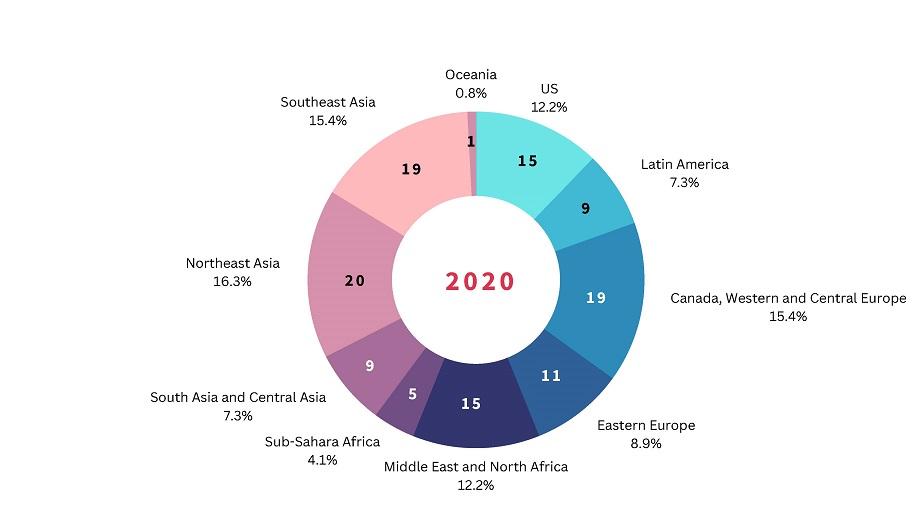
Source: Based on the Council on Foreign Relations’ Cyber Operations Tracker [4].
States have committed to combating this threat, but they need to double down and get to work. Simply ignoring it would not only allow hackers to continue their practices without retribution, but also signal to potential perpetrators that the international community is willing to turn a blind eye.
Recognising and combating the threat of economic cyber espionage means more than attribution. It also about strengthening states’ resilience to the threat through investment in domestic cybersecurity capacity and national IP systems. International cooperation in combating non-accepted forms of cyber espionage also opens up room for states and corporations to work together to develop mutual resilience through capacity-building and advocacy.
It’s all too tempting to give up in the battle to combat the threat of economic cyber espionage. But given how serious the threat is to long-term prosperity, this is certainly not the time for complacency. When companies and universities live in fear that their IP will be stolen, it affects their motivation to undertake costly, but potentially fruitful, research. Covert actors can’t be allowed to stifle progress, hinder the development of ground-breaking ideas and impede economic growth.
Article printed from The Strategist: https://aspistrategist.ru
URL to article: /combating-the-cyber-heists-that-are-costing-the-global-economy/
URLs in this post:
[1] agreed: https://www.g20.org/content/dam/gtwenty/about_g20/pdf_leaders_declaration/2015-G20-antalya-leaders-summit-communique.pdf
[2] up to $600 billion: https://www.fbi.gov/file-repository/china-exec-summary-risk-to-corporate-america-2019.pdf
[3] held: https://www.gov.uk/government/news/uk-and-allies-reveal-global-scale-of-chinese-cyber-campaign
[4] Cyber Operations Tracker: https://www.cfr.org/cyber-operations/
[5] APT 41: https://www.fbi.gov/wanted/cyber/apt-41-group
[6] research and development of critical technologies: https://techtracker.aspistrategist.ru/
Click here to print.