Cyber threats—democracy under fire on two fronts
Posted By Tom Uren on July 6, 2017 @ 11:01
National election campaigns remain vulnerable to cyber threats in two main areas, as ASPI’s International Cyber Policy Centre noted in its recent publication, Securing democracy in the digital age [1].
Political elections consist of the procedural and technical processes to collect and tally votes and the arena of ideas where policies, platforms and promises are debated and discussed. In the 2016 US presidential election, for example, attempts were made to manipulate [2] both the voting [3]apparatus [4] and the public discourse [5].
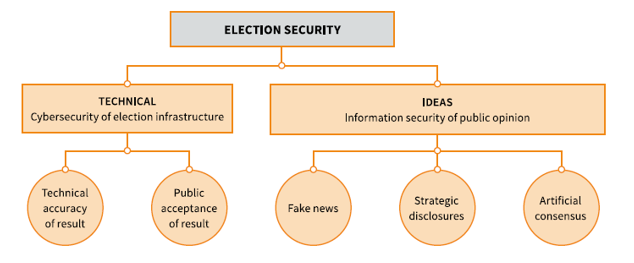
Canada’s Communications Security Establishment [6] (CSE), the counterpart of the US National Security Agency and the Australian Signals Directorate, has just released a report titled Cyber threats to Canada’s democratic process [7]. The report takes a threat modelling [8] approach to identifying election risks. That process helps people to understand and prioritise threats by identifying potential attackers and how they could carry out an attack. The report identifies possible threats (or ‘threat actors’ in security jargon)—such as hacktivists, cybercriminals, terrorists and nation-states—that might interfere with the democratic process, and assesses their motivations and capabilities.
Some can be classed as incidental threats. Cybercriminals might accidentally affect an election because they’re casting a wide net in their criminal enterprise, but are not likely to intentionally try to affect the election outcome. Hacktivists or nation-states might deliberately try to influence the outcome of an election, and CSE classifies those as strategic threats.
The report examines how threat actors might influence an election, such as through distributed denial-of-service attacks that overwhelm a site with bogus internet traffic, defacing a website, cyber-espionage and spreading fake news.
The modelling quickly identifies threats to entities involved in the election process, such as political parties, electoral commissions, voters and the media, and helps them prioritise those threats according to their consequences and likelihoods.
Understanding the environment and having an accurate assessment of the threats are key. CSE used both open-source and classified intelligence to assess threats and provides case studies that illustrate how democratic processes have been affected by cyber intrusions.
CSE assesses that hacktivist activity is all but certain at the next Canadian election in 2019. It is unsure about whether nation-states (i.e. Russia) will make an appearance, saying that will depend on how adversaries perceive Canada’s foreign and domestic policies, and on the spectrum of policies candidates espouse.
The CSE report doesn’t suggest solutions or mitigation strategies. But what can it tell us about protecting Australian democracy?
An all-source report, using both open and classified information on the threats facing Australian democracy, would be a useful start.
The Australian and Canadian situations are similar. Based on open-source reading, it’s highly likely that hacktivists will attempt to interfere with Australia’s next election. A foreign power may attempt to interfere depending on the state of politics and issues.
The Australian Electoral Commission should identify and protect high-value targets such as the electoral roll. Electoral databases are a potential point of leverage that could be manipulated or altered to swing elections or sow distrust in the system. There were widespread attempts [9] to access voting systems in the 2016 US election.
Reports by the Australian Parliament [10] and the Electoral Council of Australia and New Zealand [11] (PDF) into electronic voting options are sensibly sober, giving highest priority to security and verifiability, while also recognising that increasing the use of technology in elections is desirable for efficiency and speed. The Joint Standing Committee on Electoral Matters recommended that current paper voting systems be augmented with electronic counting, so that paper audit trails are maintained while counting speed and accuracy are increased.
A key element would be to publicise the verification and audit procedures so that Australians maintain trust in the election outcome and see any attempted hack as causing a delay within a robust process rather than throwing the whole process into doubt.
Cyber-influence operations that are designed to swing public opinion—by spreading fake news or by releasing information to tarnish reputations—are much more troubling. Those operations require relatively few resources, take advantage of freedom of speech and expression, and use the media to amplify their message. By contrast, authoritarian governments, with their control of the media and willingness to quash dissent, are practically immune. Such attacks are also highly leveraged, taking few resources to achieve large effects.
Given the relatively cheap and asymmetric nature of the threat, adversary nation-states are likely to employ it whenever it’s in their interests. And it’s easier to carry out such attacks than to prevent them. It’s hard to even decide who has responsibility for tackling cyber-influence attacks in a democracy, and we don’t yet have a ministry of truth.
A well-informed and engaged populace is a good start, so critical thinking, especially as it relates to the internet, should be in the school curriculum. Publicly exposing influence operations is crucial and should occur within a bipartisan framework developed well away from the heat of an election. In the 2016 US election, partisan politics played a key role in preventing a timely response by the Obama administration to Russian attempts [2] to influence the outcome of the poll.
Publicly exposing influence operations also raises the thorny issue of classifying information to protect sources and methods. US government information released in various cyber cases (e.g. Sony Pictures hack [12]; 2016 US election [13] (PDF)) has tended to be so vague as to be unconvincing and, given the public’s declining trust in government, it’s not effective—for some large minority of the population—for intelligence agencies to say, ‘Trust us, we know things’. But transparently revealing all your corroborating information is a terrible idea, too. Rather, it’s a case of appropriate calibration and balancing the possible future value of intelligence sources against the need to protect Western democracies from foreign interference.
Finally, we should look to the Europeans [14] for advice and inspiration. They’ve been dealing with influence operations of various sorts since World War II and have considerable expertise in countering them.
Article printed from The Strategist: https://aspistrategist.ru
URL to article: /cyber-threats-democracy-fire-two-fronts/
URLs in this post:
[1] Securing democracy in the digital age: https://www.aspistrategist.ru/publications/securing-democracy-in-the-digital-age
[2] manipulate: https://www.washingtonpost.com/graphics/2017/world/national-security/obama-putin-election-hacking/
[3] voting : https://www.bloomberg.com/news/articles/2017-06-13/russian-breach-of-39-states-threatens-future-u-s-elections
[4] apparatus: http://time.com/4828306/russian-hacking-election-widespread-private-data/
[5] public discourse: https://www.dhs.gov/news/2016/10/07/joint-statement-department-homeland-security-and-office-director-national
[6] Communications Security Establishment: https://www.cse-cst.gc.ca/en
[7] Cyber threats to Canada’s democratic process: https://www.cse-cst.gc.ca/en/democratic-process-processus-democratique/table
[8] threat modelling: https://blog.yourultimatesecurity.guide/2016/04/threat-modeling-an-introduction/
[9] widespread attempts: https://www.vox.com/world/2017/6/13/15791744/russia-election-39-states-hack-putin-trump-sessions
[10] Australian Parliament: http://www.aph.gov.au/Parliamentary_Business/Committees/Joint/Electoral_Matters/2013_General_Election/Second_Interim_Report
[11] Electoral Council of Australia and New Zealand: http://www.ecanz.gov.au/research/files/internet-voting-australian-election-systems.pdf
[12] Sony Pictures hack: https://www.fbi.gov/news/pressrel/press-releases/update-on-sony-investigation
[13] 2016 US election: https://www.dni.gov/files/documents/ICA_2017_01.pdf
[14] Europeans: http://www.smh.com.au/world/elves-v-trolls-how-europe-is-working-to-expose-russian-meddling-20170626-gwyfea.html
Click here to print.