Cyber trends in 2017: the rise of the global cyberattack
Posted By Tom Uren on December 12, 2017 @ 06:00
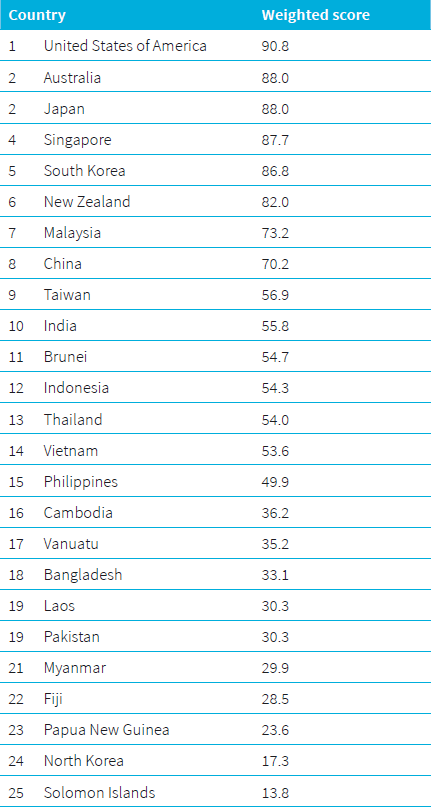
What are the mega-trends across the cyber landscape in the Asia–Pacific?
The ASPI International Cyber Policy Centre’s new report, Cyber maturity in the Asia–Pacific region 2017 [1], distils the major trends from a year’s worth of cyber events and looks at how countries in the region are measuring up to the challenges and opportunities posed by the internet and ever-more-connected IT infrastructure.
Although cyber maturity and cybersecurity generally improved over the past year, the threat landscape worsened. Cybercriminals are investing in more advanced and innovative scams, and nation-states are prepared to launch massively destructive attacks causing huge collateral damage.
The region (like other parts of the world) was affected by two state-sponsored malware attacks that were designed to cause serious damage. The WannaCry ransomware was notable for including EternalBlue (a highly advanced exploit [2] that was reportedly developed by the US National Security Agency), which allowed it to spread rapidly in many Windows environments with poor software update practices. Both the NSA [3] and Britain’s National Cyber Security Centre [4] attributed the attack to North Korea. Despite its use of sophisticated technology, WannaCry was so poorly executed that it failed to collect significant ransom money. It also contained a readily identified kill switch, which was used to prevent the malware from spreading. Even so, WannaCry affected more than 200,000 computers in over 150 countries [5], and the victims included factories, universities, and parts of Britain’s National Health Service.
The NotPetya incident, attributed to Russia, involved a Ukrainian accounting software firm. Hackers breached the software update process and used it to distribute malware to the firm’s clients using the software. The malware then spread through internal networks and wiped victims’ machines. Although it targeted Ukrainian businesses, NotPetya caused huge collateral damage [6]: German pharmaceutical company Merck reported US$310 million in direct costs and lost sales; US logistics company Fedex, US$300 million; and Danish shipping company Maersk, US$200 million. The Cadbury chocolate factory in Hobart was also shut down by NotPetya.
These events show that some states are actively and destructively using cyberweapons to gain advantage—either to raise money or to damage IT infrastructure.
The UN process that was attempting to negotiate limits on state behaviour in cyberspace broke down earlier this year without agreement. The way ahead isn’t clear. The US has talked of forming a coalition of like-minded countries that could engage in joint action, and Australia has committed to measures to respond to these threats in its International Cyber Engagement Strategy [7].
Several countries in the Asia–Pacific have started to talk more openly about military cyber capabilities. The US plans to elevate its military cyber unit [8], Cyber Command, to a unified combatant command to give it more independence and authority. Australia has established an Information Warfare Division and has declared that it has an offensive cyber capability that it’s prepared to use to disrupt and deter cyber criminals [9] targeting Australia. Japan has also proposed greatly expanding its military cyber investment, albeit from a very small base.
Although militaries traditionally shroud their cyber capabilities in secrecy, more transparency and doctrine-sharing would be welcome. Increased openness, collaboration, and other confidence-building measures would help to set expectations of state behaviour, clarify how international law applies, and reduce the risk that cyber incidents will result in accidental escalation into armed conflict. Australia has led the way in this area; it is relatively transparent about its cyber offensive capabilities and has consistently emphasised that both international and domestic law applies in offensive cyber operations.
Cybercrime is also a huge issue in the region. With the rise of ‘crime as a service’, the technical sophistication needed to be a cybercriminal is lower than ever. The rewards are high and the chances of arrest are low. As countries in the region become better connected to the internet, rising levels of cybercrime threaten to undermine progress on economic development enabled by the internet. But government regulation and law enforcement make a difference. Tonga is a shining example—it became the first Pacific island to accede to the Budapest Convention on Cybercrime, a treaty that enables a cross-border approach to tackling cybercrime.
In a third worrying development, many countries use cybersecurity laws to impose or strengthen information control and censorship. Of the 25 countries covered in our report, just four—Australia, Japan, the Philippines and the United States—are classified as having a free internet [10].
Overall, cyber maturity improved across all countries in the region: governance, law enforcement and international engagement are stronger, and the internet is available to more people. But progress is uneven. The countries that lead in cyber maturity—the US, Australia, Japan, Singapore and South Korea—continue to pull away from less developed countries that struggle to invest in cybersecurity and telecommunications in the face of more pressing economic and human development concerns.
The spread of the internet provides huge development opportunities, but it also comes with its fair share of challenges. Australia and other developed countries in the region must directly address the challenges of dangerous state behaviour, the spread of cybercrime, and a constrained and censored internet, by promoting our vision of a free, open and secure internet that will benefit all economies in the region.
Article printed from The Strategist: https://aspistrategist.ru
URL to article: /cyber-trends-in-2017-the-rise-of-the-global-cyberattack/
URLs in this post:
[1] Cyber maturity in the Asia–Pacific region 2017: https://www.aspistrategist.ru/report/cyber-maturity-asia-pacific-region-2017
[2] exploit: https://en.wikipedia.org/wiki/Exploit_(computer_security)
[3] NSA: https://www.washingtonpost.com/world/national-security/the-nsa-has-linked-the-wannacry-computer-worm-to-north-korea/2017/06/14/101395a2-508e-11e7-be25-3a519335381c_story.html
[4] National Cyber Security Centre: http://www.bbc.com/news/technology-40297493
[5] 200,000 computers in over 150 countries: https://www.reuters.com/article/us-cyber-attack-europol/cyber-attack-hits-200000-in-at-least-150-countries-europol-idUSKCN18A0FX
[6] huge collateral damage: https://www.cyberscoop.com/notpetya-ransomware-cost-merck-310-million/
[7] International Cyber Engagement Strategy: http://dfat.gov.au/international-relations/themes/cyber-affairs/aices/index.html
[8] elevate its military cyber unit: https://www.defense.gov/News/Article/Article/1283326/dod-initiates-process-to-elevate-us-cyber-command-to-unified-combatant-command/
[9] deter cyber criminals: https://www.pm.gov.au/media/offensive-cyber-capability-fight-cyber-criminals
[10] having a free internet: https://freedomhouse.org/report/freedom-net/freedom-net-2017
Click here to print.