Doxxing the pro-democracy movement in Hong Kong
Posted By Elise Thomas on October 1, 2019 @ 15:11

Since late August, an anonymous website [1] has been publishing the personal details of pro-democracy protesters, journalists and politicians in Hong Kong. Building on our team’s earlier analysis [2] of the state-backed information campaign targeting the Hong Kong protests, I took a look at how this site has been spread on Twitter.
Not enough evidence has been found to attribute responsibility for the site directly to a person or an entity. However, here’s what can be said with confidence about the site and the efforts to spread it on Twitter:
- It targets the pro-democracy movement in Hong Kong, with a clear intention to intimidate and incite harassment.
- It was propagated on Twitter using accounts similar to those previously taken down by the platform for coordinated inauthentic behaviour linked to state-backed actors. This includes:
– multiple accounts created or activated on 26 August, three days before the ‘hkleaks.org’ domain went public on Twitter
– some content which appears to have been prepared at least seven days in advance
– active efforts to avoid Twitter’s automated detection of links to the site. - It uses personal information which some of those affected say could only have come from official sources.
- It features customised, professional-quality graphic design, indicating an investment in time and resources.
- It found a new hosting provider within days after being shut down for unknown reasons.
- It has been promoted by official Chinese state media, as well as on the social media accounts of mainland Chinese police and other institutions.
- It is continuing to expand, including adding new individuals, categories and videos to the site.
Background
The personal details being posted in this doxxing campaign include headshots, dates of birth, telephone numbers, social media accounts, home addresses and a record of ‘nasty behaviours’ such as participating in protests, covering protests as a journalist or not paying public transport fares (a tactic some protesters have been using in order to avoid being tracked). The website is an unambiguous attempt at intimidation—the faces of those featured on the site are pictured in crosshairs.

Screenshot from the site of a protester’s face pictured in crosshairs with a stamp translating as ‘thug’ (we have blurred this person’s face to avoid further violating their privacy).
Some of those whose information has been featured on the site say those details could only have come from official government sources. Photos, addresses and phone numbers supplied to the mainland Chinese police and Chinese government–affiliated China Travel Service (Hong Kong) Limited were reportedly [3] included on the site.
On 18 September, the state broadcaster, China Central Television (CCTV), published a video about the site on its official Weibo account, encouraging viewers to ‘pull off the mask’ of ‘rioters’ in Hong Kong by submitting information to the hkleaks.ru site. The report has since been spread widely across dozens of smaller Chinese media sites, as well as social media platforms like WeChat, Weibo, WhatsApp and, to a lesser extent, Facebook, including on the official channels of police agencies and Chinese Communist Youth League branches.
A concurrent doxxing campaign is also taking place on the Telegram app that’s aimed at identifying Hong Kong’s pro-democracy protesters and rioters and supplying that information to China’s mainland Ministry of State Security Reporting Platform, as documented by [4] the Atlantic Council’s Digital Forensic Research Lab.
Domain change
The creators of the doxxing site have taken steps to keep it online and to obscure who is behind it. The site was first registered on 16 August at hkleaks.org using a Canadian host and appears to have gone public on or around 30 August. It went down on 4 September, only to be re-registered at hkleaks.ru on 6 September. The site is now hosted at a Belize IP address and supported by Russian hosting service provider Dancom, which also trades under the name DDoS-GUARD.
As the name suggests, DDoS-GUARD offers its clients protection against distributed denial-of-service attacks. The choice of provider may indicate that those behind the site were anticipating potential retaliation from pro-democracy supporters, including DDoS attacks against the site. Perhaps more significantly, by hosting the site in Belize via a Russian company, the likelihood of diplomatic, political or legal pressure to take it down may be significantly lower than in a jurisdiction like Canada.
Interestingly, however, the site is in clear violation of DDoS-GUARD’s acceptable use policy [5], which prohibits ‘threats of physical harm’ and material that is ‘excessively violent, incites violence, threatens violence, or contains harassing content or hate speech’ that ‘violates a person’s privacy’. It also bans ‘posting private information about a person without his or her consent’.
Propagation on Twitter
To its credit, Twitter has removed many of the early efforts to share the hkleaks site on its platform. While this is obviously a good outcome, it prevents a comprehensive analysis of the tactics and methods used to propagate the site. However, enough evidence remains to draw at least some broad findings.
The remaining accounts used to promote the site bear notable similarities to those which our team analysed after they were taken down by Twitter for coordinated inauthentic behaviour. The earlier information campaign included both accounts that appeared to have been created specifically for the purpose of targeting the Hong Kong protests, and ‘vintage’ or ‘aged’ accounts. These aged accounts often lie dormant for years before being passed on or sold to new owners, often for spam or marketing purposes, since older accounts appear more authentic than brand new ones.
Both types of accounts also appear to have been involved in promoting the doxxing site. Several of the remaining accounts that promoted the site were created or became active on 26 August, a few days before the original hkleaks.org site began to be publicly promoted.
For example, the account @ellaliu13846289, which was created on 26 August, has posted exclusively about the Hong Kong protests in both English and Chinese, including vilifying the pro-democracy protesters as thugs, rioters and terrorists, and boosting conspiracy theories about Western and US funding for the protests, both of which were major narratives promoted by the Chinese-state-backed information operation.
The account began promoting the original hkleaks.org site on 12 September (based on remaining tweets; it’s possible that earlier tweets have been deleted).
This is particularly interesting because 12 September is after the hkleaks.org site was deleted, meaning that the content including screenshots must have been prepared at least a week in advance, before the site was taken down.
This would be very strange thing for a normal Twitter user to do. Preparing and scheduling content days in advance, however, is the kind of behaviour which could make sense in the context of a planned information operation—and might explain an account’s operators forgetting to update it if some small but crucial detail, like the domain name, were to change.
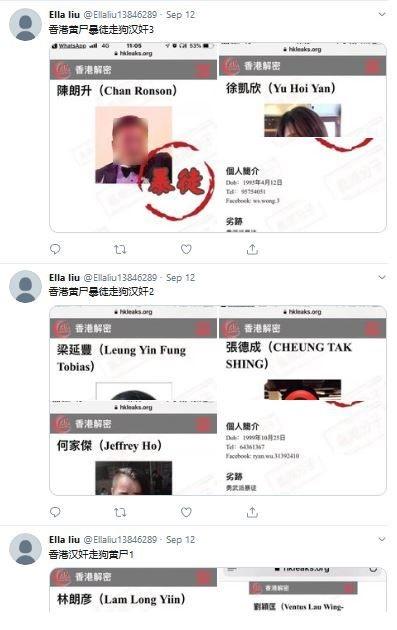
Tweets featuring screenshots from hkleaks.org posted on 12 September, referring to protesters as “Hong Kong ‘Yellow Zombie’-Thug-Running Dog-Race Traitors”. Yellow Zombie is a homonym for Yellow Ribbon—a symbol of the pro-democracy movement in Hong Kong.
The account @madisontomas1 was also created on 26 August. It posted links to a video posted on a separate platform showing the doxxing site, and links to the new domain, hkleaks.ru, on 19 September, the day after CCTV promoted the site. The account holder has pinned the video to the top of their timeline.
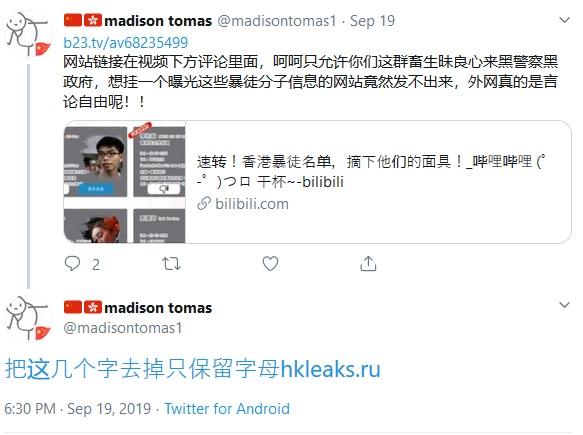
Tweet linking to video of the doxxing site on another platform. Tweet reads: ‘The link to the website is in the comments under the video. Ha ha, you animals are only allowed to unconscionably blacken the name of the police and the government. If you try posting a link to a website that exposes these thugs, it can’t be sent out. There really is so much free speech on the global internet!!’
As an example of an aged account, @amnestyinchina was created in June 2015, but didn’t make its first tweet until—you guessed it—26 August, the same day the two accounts discussed above were created. On 17 September, the account began promoting hkleaks.ru, and also pinned a tweet about the site to the top of its profile.
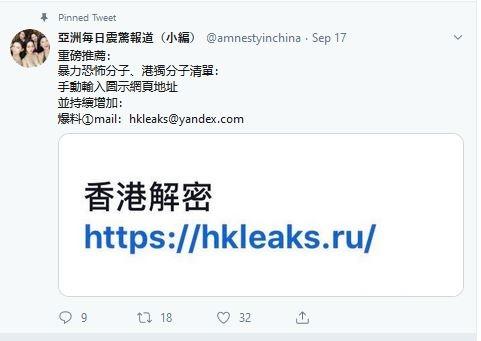
Tweet promoting the site and encouraging Twitter users to send additional leaks and data to the site via the email address [email protected].
The accounts that remain online have employed a number of tactics that appear to be designed to prevent Twitter from automatically detecting and removing links to the site (which may be why these particular tweets are the survivors). This includes introducing spaces or additional characters into the links, by using ‘hkleaks . ru’ or ‘hkleaks[.]ru’, for example, as well as putting the link in an image file, as shown in the above tweet from @amnestyinchina.
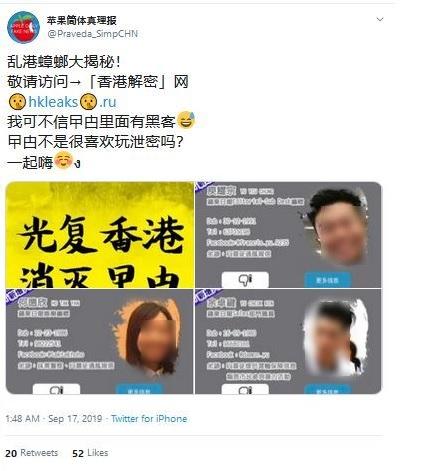
Tweet using emojis to break up the site URL. Tweet reads: ‘Chaos-causing Hong Kong cockroaches unmasked! Please visit →「Hong Kong Decrypted」website 🤫hkleaks🤫.ru
Who’d have thought there were hackers among the cockroaches. The cockroaches do like leaking things after all, right? Let’s do this!☺ง’
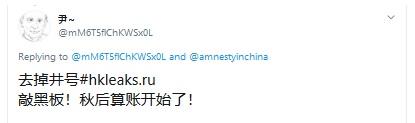
Tweet using a hash symbol to break up the link. The tweet advises users to remove the hash symbol.
While not enough evidence has been found to identify who is responsible for creating and spreading the site, what we can say is that whoever is behind this doxxing campaign appears to be well resourced and well organised, and allegedly has access to information gathered by official sources. They are seeking to intimidate and undermine pro-democracy protesters, journalists and other individuals, and they are actively attempting to use social media, including Western platforms like Twitter, to do it.
This campaign against the pro-democracy movement is ongoing. In recent days the site has continued to add profiles, new categories and video footage of the protests. As the situation in Hong Kong becomes ever more extreme, Western social media companies must remain alert to the evolving tactics of those who seek to use their platforms as a weapon against the pro-democracy movement.
Article printed from The Strategist: https://aspistrategist.ru
URL to article: /doxxing-the-pro-democracy-movement-in-hong-kong/
URLs in this post:
[1] an anonymous website: https://www.buzzfeednews.com/article/rosalindadams/hong-kong-doxing-protesters-china-encourage
[2] our team’s earlier analysis: https://www.aspistrategist.ru/report/tweeting-through-great-firewall
[3] reportedly: https://advox.globalvoices.org/2019/09/19/china-central-television-urges-netizens-to-doxx-hong-kong-protesters-and-reporters/
[4] as documented by: https://medium.com/dfrlab/telegram-channels-used-to-doxx-and-report-hong-kong-protesters-to-chinese-authorities-91bed151f345
[5] acceptable use policy: https://ddos-guard.net/file/aup_en.pdf
Click here to print.